GiS mbH
Höllochstraße 1
D - 73252 Lenningen
Tel: +49 (0) 7026 - 606 - 0
Fax: +49 (0) 7026 - 606 - 66
e-mail: rfid@gis-net.de
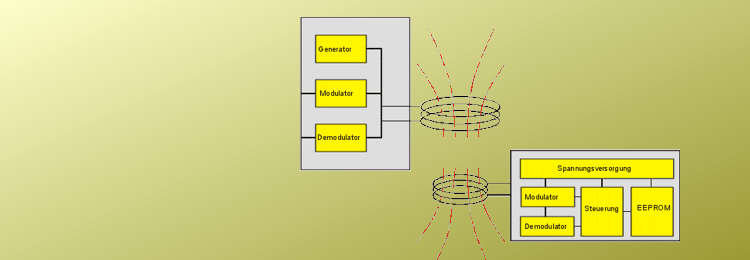

How are RFID-Tag properly aimed ?
Restriction of the reading / write reach:
Again and again, wrong alignments of the transponder to the antenna lead to read or range problems.
These can also by the direct mounting of the transponder on metal accrue.
It is therefore important to ensure that, between metal surface and transponders at least 8 mm is maintained.
Multiple programming:
When programming transponder must be taken to ensure that crosstalk is prevented to adjacent transponders.
This can be a sufficient distance from at least 10 cm should be avoided between the transponders or
by a cover adjacent transponders using a metal template.
What is a RFID-Tag ?
A RFID-tag is a microelectronic circuit with transmit- and receive-antenna,
with a control-unit and a data- and energy-memory. These circuits exist in several types of housings, for example as stick-label,
button, chip-card, stick, bracelet, screw or badge. The housing is hermetically sealed and are very robust and resistant against shock,
vibration, pressure , chemicals and temperature.
There are two different systems of data medium: The first type can be programmed only once (unique), the second one allows an
exchange or overwriting of the stored information (programmable transponder).
Additionally RFID-tags can be distinguished between active and passive systems. Active systems take the required energy for
the transmission of information from a battery, passive ones from a electromagnetic field (battery-free systems).
A great variety of applications exist for RFID-technology.
Identification with RFID-tags (transponder) makes sense in closed production or assembling circles or when you have the
necessity to update and change the information stored in the tag during the service live.
GiS realized applications in multiple industrial sectors, as waiter lock systems, identification of film emulsions in darkrooms,
control of bottling plants, conveyor systems in the automobile production and many more.
One examples is described in the following more detailed:
Replacement of barcode reader by RFID-systems in textile sorting plants.
How does a RFID-tag work ?
If a tag enters the range of the read/write-antenna, first the
energy memory of the battery-free tag is loaded. After that the RFID-tag transmits the contents of it's data-memory
to the read/write-station, or it gets new ones which are stored. The dialogue resp. the data-transfer is repeated
cyclically as long as the transponder takes place in the range of transmission. The security during the transmission
is ensured by a appropriate data-protocol.
The range of data transmission depends on the antenna-size of the tag, the read/write-station and if it is a
transponder of the active or passive type. Active transponders can have a range up to 100 meters whereas
passive ones have a range between
2 and 70 cm.
Where are RFID-Tag used ?
Identification with RFID-technology distinguishes itself by great security and robustness.
There is no wear because of contact less reading the tags without visual contact. The tags themselves can be located at inaccessible places.
They can be encapsulated into plastic to make them insensitive against harsh environments. It is even possible to implant the tags in the
original material of the product himself. For example embedding the tag into a tyre or the outer skin of a boat. Neither humidity nor dirt
have negative effects to the function, this means total maintenance-freeness.
Automatic identification can be - depending on the used components - extremely fast, transport or reading velocities up to 3m/s are possible.
Simultaneous reading of several tags is also possible, this allows fast processing, for example in conveyor systems.
The most interesting characteristic of RFID-technology is the possibility of overwriting or supplementing the stored data in the tag.
For example it is possible to assign certain data to a work piece, these data are used for the next step of processing. Or you store
a value on a chip card, which is debited when the card is used, for example in an automatic retailer. You don't need a connection to
a host computer, the reader himself makes the debit, which means to overwrite the data in the chip card.
Altogether, RFID-technology is an extremely flexible means for automatic identification of people or components - inexpensive, secure, fast and reliable.
